Blog
Best Practices to Enhance Cloud Contact Center Security with Google Cloud
12 min read

The switch to cloud-based contact centers has enhanced customer service by allowing greater flexibility and cost savings. However, this change implies a fundamental commitment to protect sensitive client data, as security breaches can result in significant financial losses, reputation, and regulatory concerns. Google Cloud provides security capabilities that help businesses build secure cloud contact centers, offers network security, access control, and data centers, thus ensuring the cloud is secure.
Understanding Cloud Contact Center Security Issues
To effectively address security concerns, we must first identify potential risks.
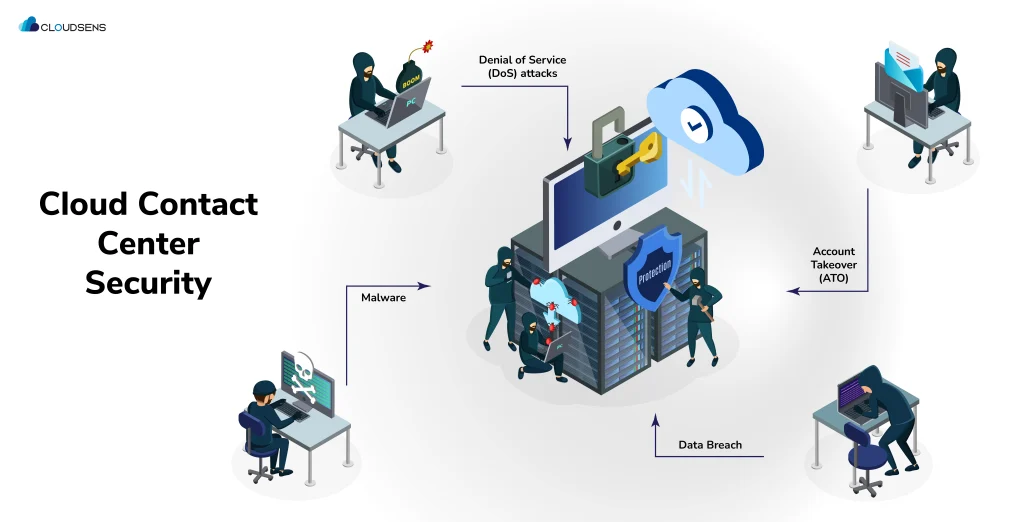
Data Breach
Unauthorized access to sensitive customer information, such as names, phone numbers, and call logs, can have devastating effects.
Denial of Service (DoS) attacks
These attacks can lead to loss of money, disrupt contact center services, and affect customer service
Account Takeover (ATO)
Malicious professionals may attempt to take over accounts, destroy customer data, and disrupt services.
Malware
Compromised contact center systems have the potential to reveal sensitive information and create vulnerabilities that can be misused by cyber criminals.
Google Cloud's Security Features
Google Cloud offers robust security features, such as:
Data Encryption
Data is encrypted both in transit and at rest to provide security against unauthorized access.
Identity and Access Management (IAM)
Only authorized users can access specific resources by implementing access restrictions with fine-grained control.
Cloud Security Command Center
The Security Command Center (SCC) helps you identify, investigate, and respond to threats, reducing security risks.
Compliance Certifications
Google Cloud adheres to industry-standard compliance certifications, providing you peace of mind when making decisions about data security.
Regular Security Planning
Train your contact center’s administrators and staff on security best practices, including recognizing phishing attempts, reporting unusual behavior, and creating strong passwords.
Maintain System Redesigns
To address security vulnerabilities, all contact center software and core systems should be regularly redesigned.
Data Security Organization
Implement data security policies to regulate data classification, support, and exchange. Ensure adherence to data security controls like GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act).
Conduct Security Audits
Perform regular penetration tests and security audits to identify any potential vulnerabilities in your cloud contact center configuration.
Cloud Data Loss Prevention (Cloud DLP)
Utilize Cloud DLP activity to proactively identify and mitigate risks from potentially unstable content that might suddenly surface or that could be revealed through emails, chat rooms, or other channels of communication
Zero Trust Network Access (ZTNA)
ZTNA may be used to continuously authorize and grant access to contact center resources, regardless of user location.
Working with Google Cloud for Peak Security
By leveraging Google Cloud’s robust security capabilities and adhering to these best practices, businesses can create extremely secure and reliable cloud contact centers. Working with Google Cloud might enhance security in the following ways:
Implement Incident Response Planning
To make sure you are prepared for a security incident, implement incident response strategy into practice. This includes forming an emergency management team, carrying out routine exercises and drills, and developing an incident response plan.
Additional Security Considerations
Employee Offboarding:
Establish a secure offboarding process to revoke access privileges and protect sensitive information. Regularly perform security audits and assessments to identify vulnerabilities and areas that need improvement.
Business Continuity and Disaster Recovery:
Develop a thorough BCDR strategy to ensure business continuity in case of security incidents.
Building a Security Culture
A strong security culture is fundamental to the long-term success of your contact center. Encourage employees to report suspicious activities and provide ongoing security awareness training. Fostering a culture focused on security can greatly lower the chances of security breaches.
Integrating AI and Machine Learning for Security
Artificial Intelligence (AI) and Machine Learning (ML) are powerful tools in enhancing contact center security. By using this technology, we can analyze large amounts of data to detect unusual patterns and possible threats. For instance, by monitoring call patterns AI can help in identifying fraudulent activities. Machine Learning models can enhance their performance over time by identifying and reducing the emerging threats. Integrating AI and ML into your security plan can offer a preventive method for identifying threats and lower the chances of security issues in contact centers.
Security Information and Event Management (SIEM)
Integration of Security Information and Event Management (SIEM) systems improves security measures. SIEM solutions provide real time security alerts generated by network hardware and applications. Organizations can gain a complete understanding of their security status, quickly detect and respond to issues, and ensure compliance with regulatory requirements by integrating SIEM. This integration facilitates linking events across multiple sources, identifying suspicious activities, and automating responses to reduce threats promptly.
Regular Security Drills and Simulations
Conducting regular security drills and simulations is an essential practice to ensure that your contact center staff are well-prepared for potential security incidents. These drills identify weaknesses in your current security protocols and provide an opportunity for continuous improvement. By simulating various attack scenarios, such as phishing attempts, DoS attacks, and data breaches, your team can practice responsive strategies and refine them based on real-world conditions. This proactive approach ensures that your staff can respond quickly and effectively, minimizing the impact of security incidents on your operations and customer trust.
Emphasizing Physical Security Measures
While digital security is important, physical security measures should not be overlooked in a cloud contact center environment. Safeguarding your physical infrastructure, including data centers and office spaces, from unauthorized access is crucial. Implement access control systems, surveillance cameras, and security personnel to safeguard sensitive areas. Additionally, enforce policies that restrict access to critical hardware and ensure that employees adhere to strict security protocols when handling sensitive information. By integrating physical security measures with your overall security strategy, you can create a comprehensive defense against potential threats.
Conclusion
Security should be a top priority in every cloud contact center solution. This is not just about building trust with customers, but also protecting sensitive data, ensuring regulatory compliance, and ultimately boosting the effectiveness of your cloud contact center. By staying informed about emerging security trends and threats, implementing robust security measures, and prioritizing security, CloudSens enables you to create a secure and reliable cloud contact center environment that meets the needs of your customers and your business.
FAQ
1. Why is security essential for cloud contact centers?
Safeguards sensitive customer data, ensures regulatory compliance, and maintains trust, which is essential for operational integrity
2. What specific security features does Google Cloud offer for contact centers?
Data encryption, Identity and Access Management (IAM), and Security Command Center for comprehensive security.
3. How can AI and machine learning improve contact center security?
Detect unusual patterns, prevent fraud, and identify emerging threats by analyzing large datasets in real time.
4. What is the purpose of Security Information and Event Management (SIEM) in contact centers?
SIEM systems centralize security alerts, identify suspicious activities, and enable automated responses to potential threats
Our Recent Blogs

What are Cloud Contact Center Solutions?
What is Google Cloud Platform?

Best Practices to Enhance Cloud Contact Center Security with Google Cloud
